TryHackMe | Introduction To Honeypots Walkthrough
A guided room covering the deployment of honeypots and analysis of botnet activities
Link- https://tryhackme.com/room/introductiontohoneypots

Create a file and then log back in is the file still there? (Yay/Nay)
Nay
How many passwords include the word “password” or some other variation of it e.g “p@ssw0rd”
15
What is arguably the most common tool for brute-forcing SSH?
hydra
What intrusion prevention software framework is commonly used to mitigate SSH brute-force attacks?
Fail2Ban
What CPU does the honeypot “use”?
Run command cat /proc/cpuinfo
Intel(R) Core(TM) i9–11900KB CPU @ 3.30GHz
Does the honeypot return the correct values when uname -a is run? (Yay/Nay)
Nay
What flag must be set to pipe wget output into bash?
-O
How would you disable bash history using unset?
unset HISTFILE
What brand of device is the bot in the first sample searching for? (BotCommands/Sample1.txt)
Do a simple google search of the processes
Mikrotik
What are the commands in the second sample changing? (BotCommands/Sample2.txt)
root password
What is the name of the group that runs the botnet in the third sample? (BotCommands/Sample3.txt)

Google search for mdrfckr
Outlaw
What application is being targetted in the first sample? (Tunnelling/Sample1.txt)
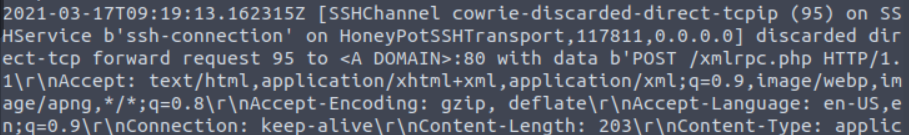
Google search for xmlrpc.php
WordPress
Is the URL in the second sample malicious? (Tunnelling/Sample2.txt) (Yay/Nay)
Nay
That’s it ! See you in the next Room :)
Comments
Post a Comment