TryHackMe | Linux Server Forensics Walkthrough
Learn about digital forensics artefacts found on Linux servers by analysing a compromised server
Link:- https://tryhackme.com/room/linuxserverforensics
Deploy the first VM
Login using ssh and navigate to /var/log/apache2
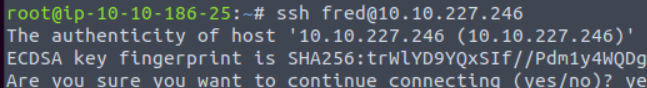

How many different tools made requests to the server?
Run the below command
Answer is 2
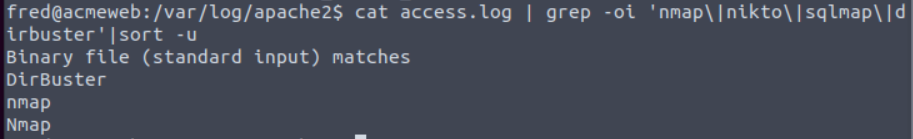
Name a path requested by Nmap.
Run below command
Answer is /nmaplowercheck1618912425
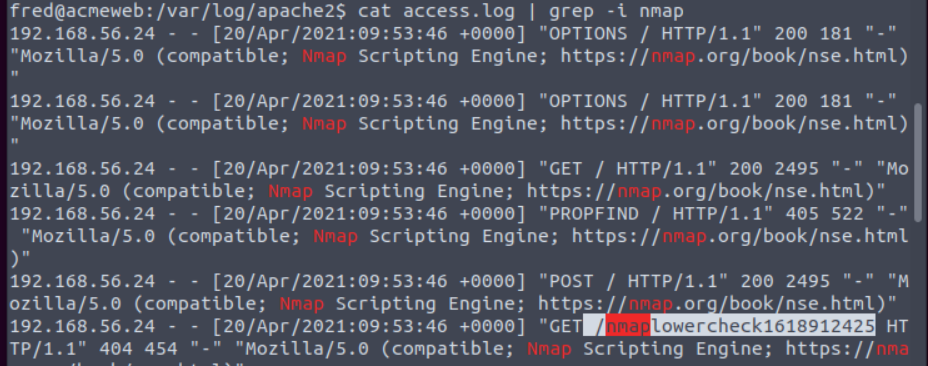
What page allows users to upload files?
Navigate to the website

Answer is contact.php
What IP uploaded files to the server?
Run below command to find

Answer is 192.168.56.24
Who left an exposed security notice on the server?
Run below command to find
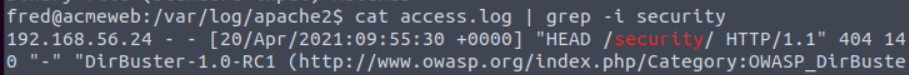
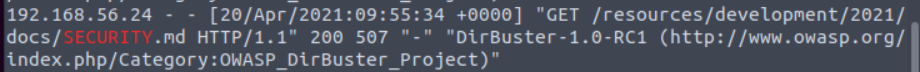
Go to the location mentioned above and open the security.md file
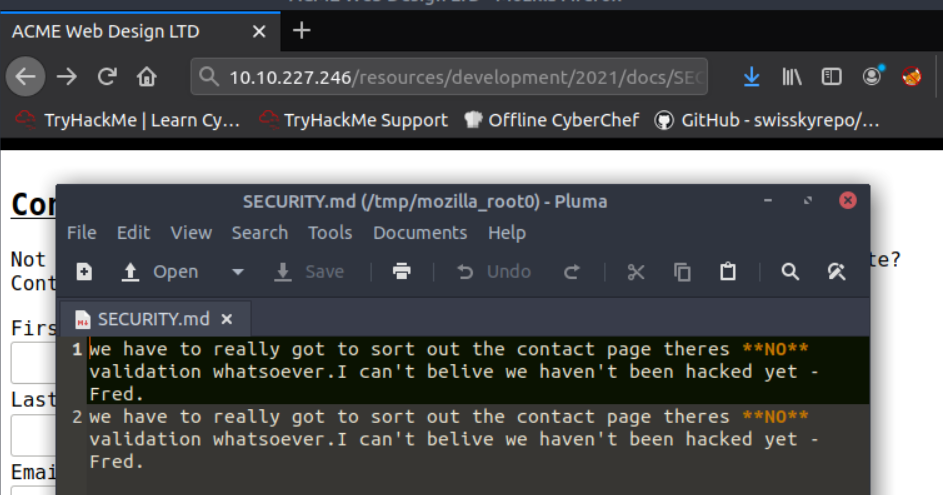
Answer is Fred
What command and option did the attacker use to establish a backdoor?
Run below command to find backdoor

Answer is sh -i
What is the password of the second root account?
Search passwd
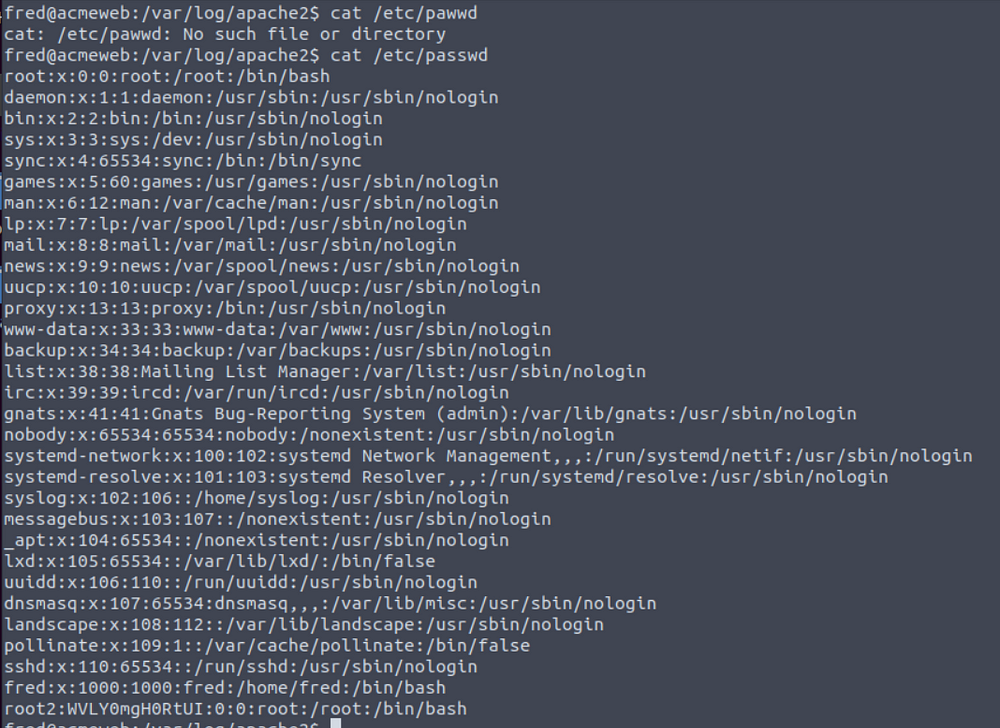
Google search xxx from root2 :xxx to find password
Deploy the second VM
Login and navigate to logs
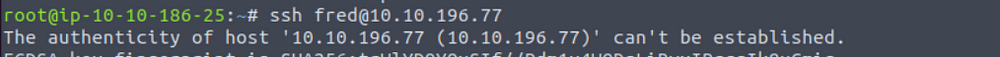
Name one of the non-standard HTTP Requests.
Run below command
Answer is gxwr
At what time was the Nmap scan performed? (format: HH:MM:SS)
Non standard method gxwr -nmap
Answer is 13:30:15
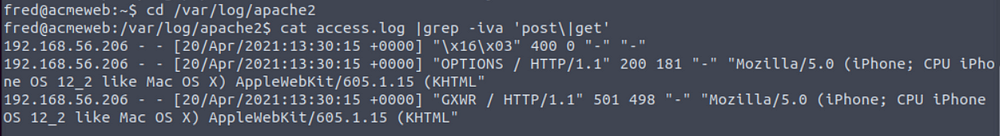
What username and hostname combination can be found in one of the authorized_keys files? (format: username@hostname)
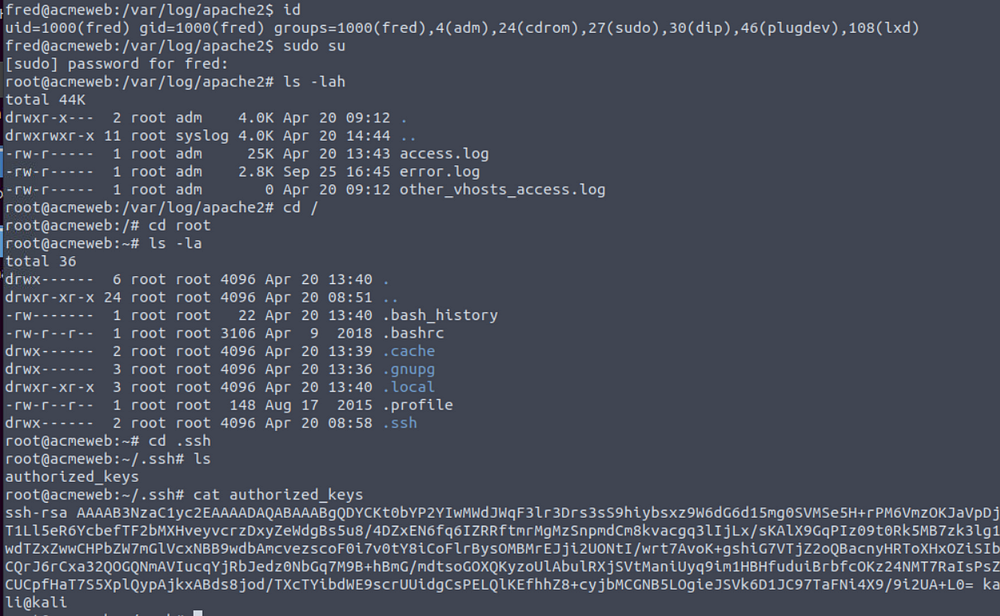
Answer is kali@kali
What is the first command present in root’s bash_history file?
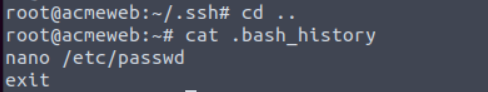
nano /etc/passwd
Deploy The Final VM
Login
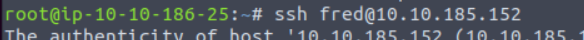
Run below command

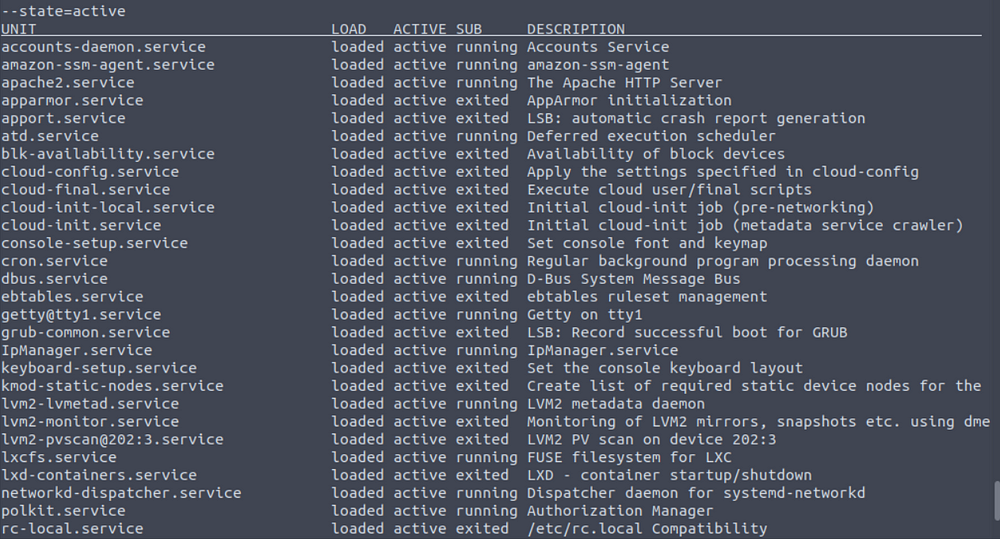
Figure out what’s going on and find the flag.
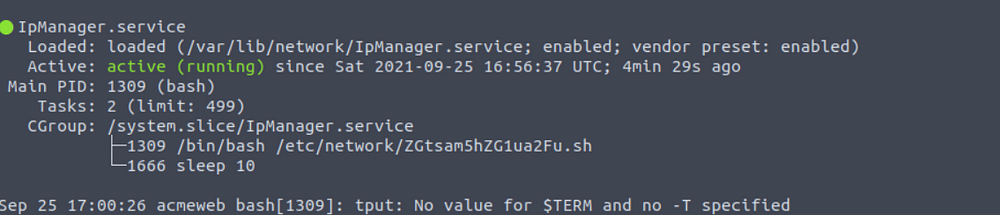
Run systemctl status IpManager.service
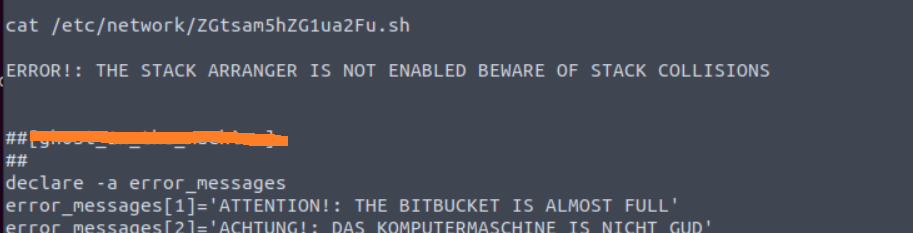
Open the file /etc/network /ZGtsam5hZG1ua2Fu.sh
This will show the flag
That’s it! See you in the next room :)
Comments
Post a Comment